Helping Businesses
to Become Iconic
Brands
We have become the top-notch software development services provider primarily due to our.
Our Top Services
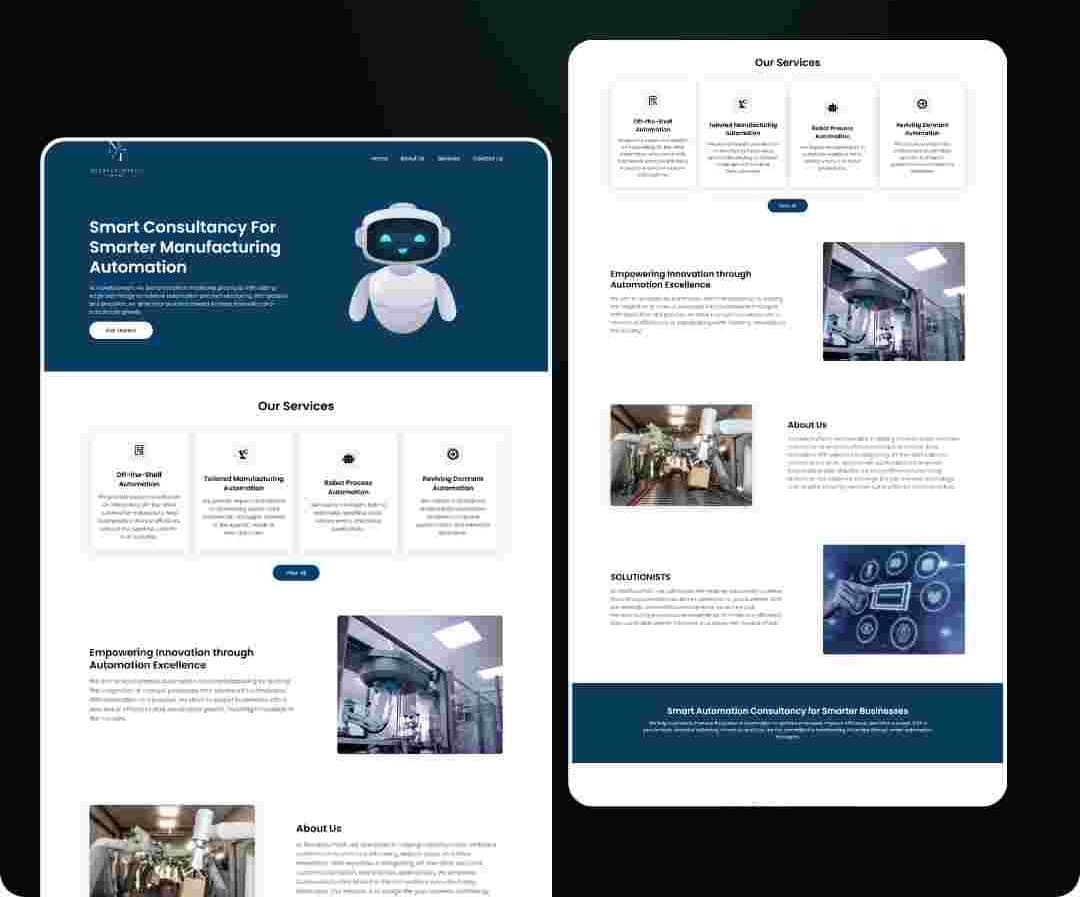
Web Design & Development
Your website is often the first impression you make. We build fast, mobile-friendly websites that help your visitors find what they need, trust your brand, and take action.
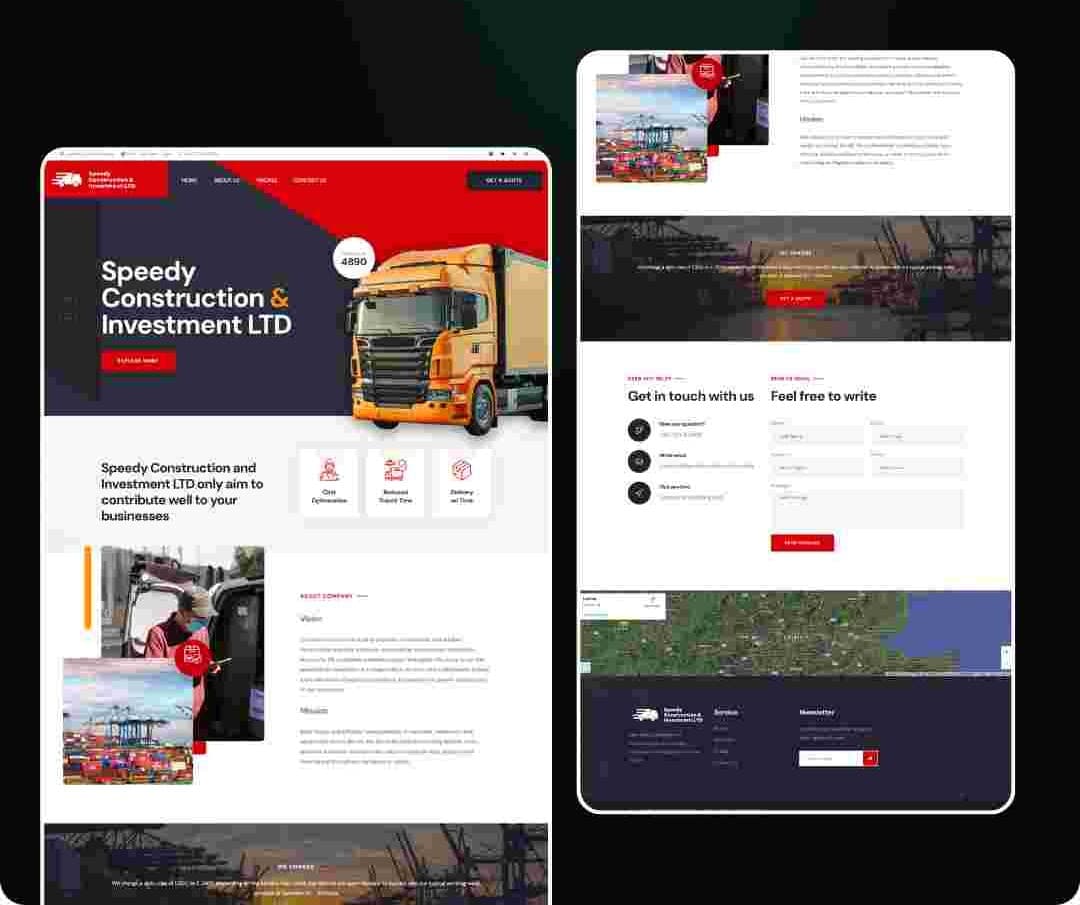
Web & Mobile App Development
We build smart, user-friendly apps that deliver practical solutions—whether it’s streamlining operations, improving customer experience, or bringing your ideas to life.
Digital Marketing
We craft tailored digital strategies that offer real solutions—helping you reach the right audience, build trust, and grow your business online.
Why Choose Us?
Reliable Solutions: EZ Brand Builders understands that every business is unique. We serve them with innovative solutions that help them overcome business challenges.
Client-Centric Approach: We always ensure our client’s mission and work accordingly to drive business growth.
Constant Support: Our goal is to give businesses peace of mind and allow them to concentrate on their primary business operations by offering continuous support and maintenance.
Depth of Knowledge: We use our expertise to guide our clients through the challenges of the digital age and assist them in achieving their strategic objectives.

0+
Happy Clients
0+
Solutions Proposed
0%
Clients Retention Rate
0%
Client Satisfaction Rate
Our Development Process
Exceptional development. Seamless integration. Delighted developers. Increased adoption.

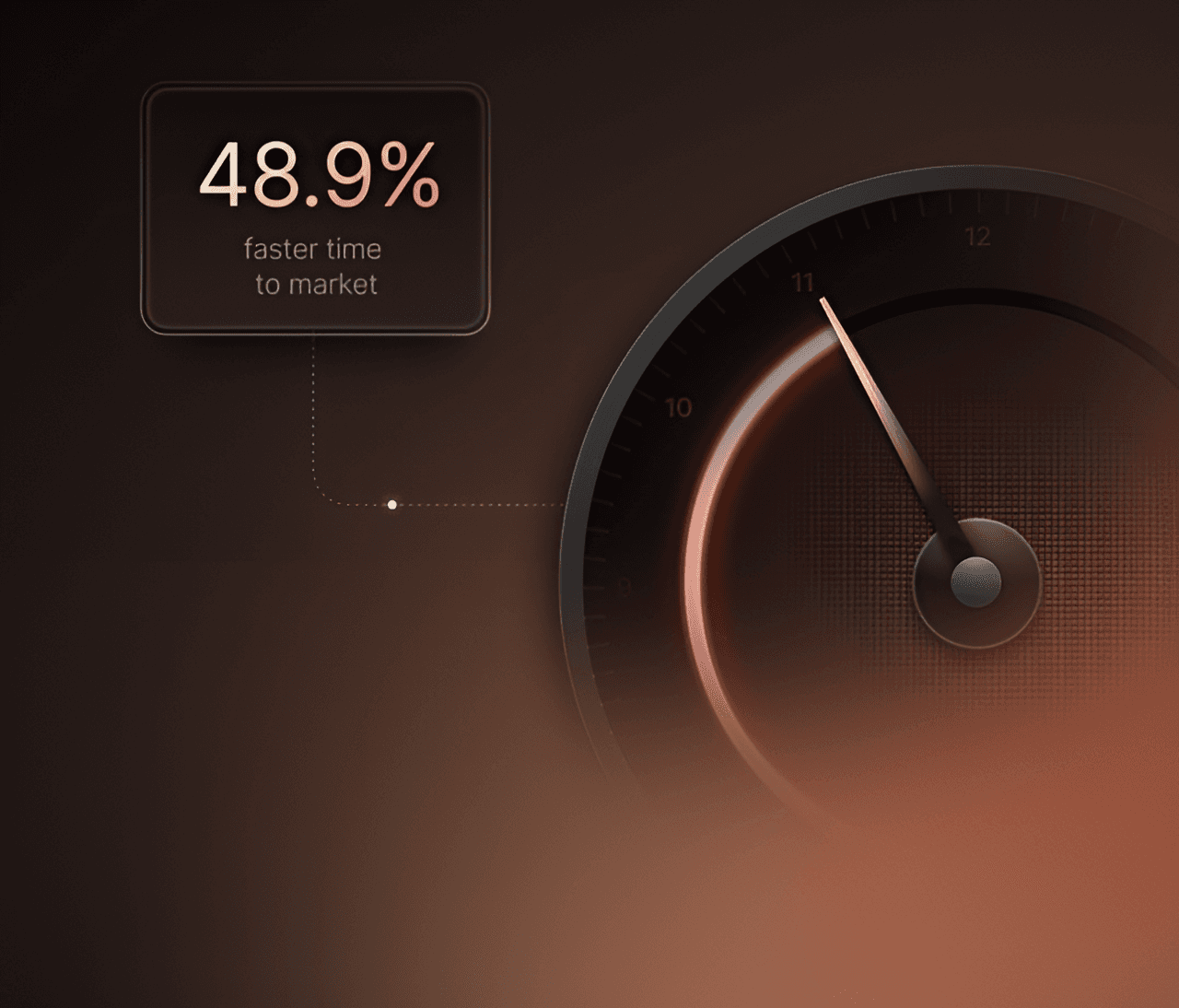
Accelerate time-to-market
descriptionGet your product to market faster with our SDK development services. Reduce time-to-market from months to weeks.
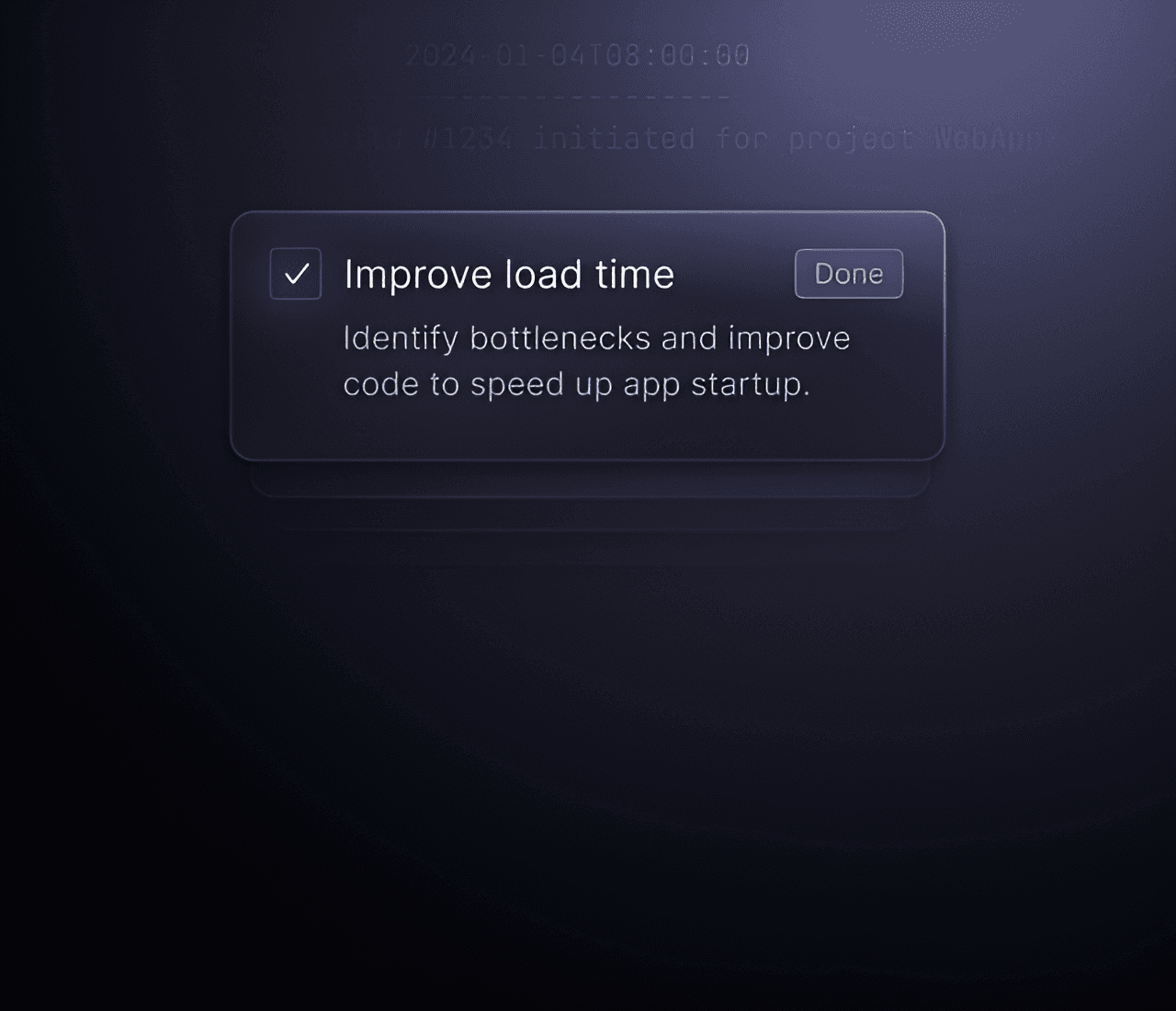
Reduce development costs
Minimise development costs for your customers and internal teams. Well-designed SDKs save valuable time and resources.
Boost app quality and stability
Develop SDKs that empower developers to build stable, performant, and secure applications, leading to a better user and developer experience.

Foster developer ecosystem
Empower developers with clear documentation, intuitive APIs, guides, samples, and tutorials – to accelerate product adoption and diversify integrations.


Our Clients
We take pride in our diverse clientele, ranging from startups to established enterprises. Our clients trust us to deliver innovative solutions that drive their business forward.





























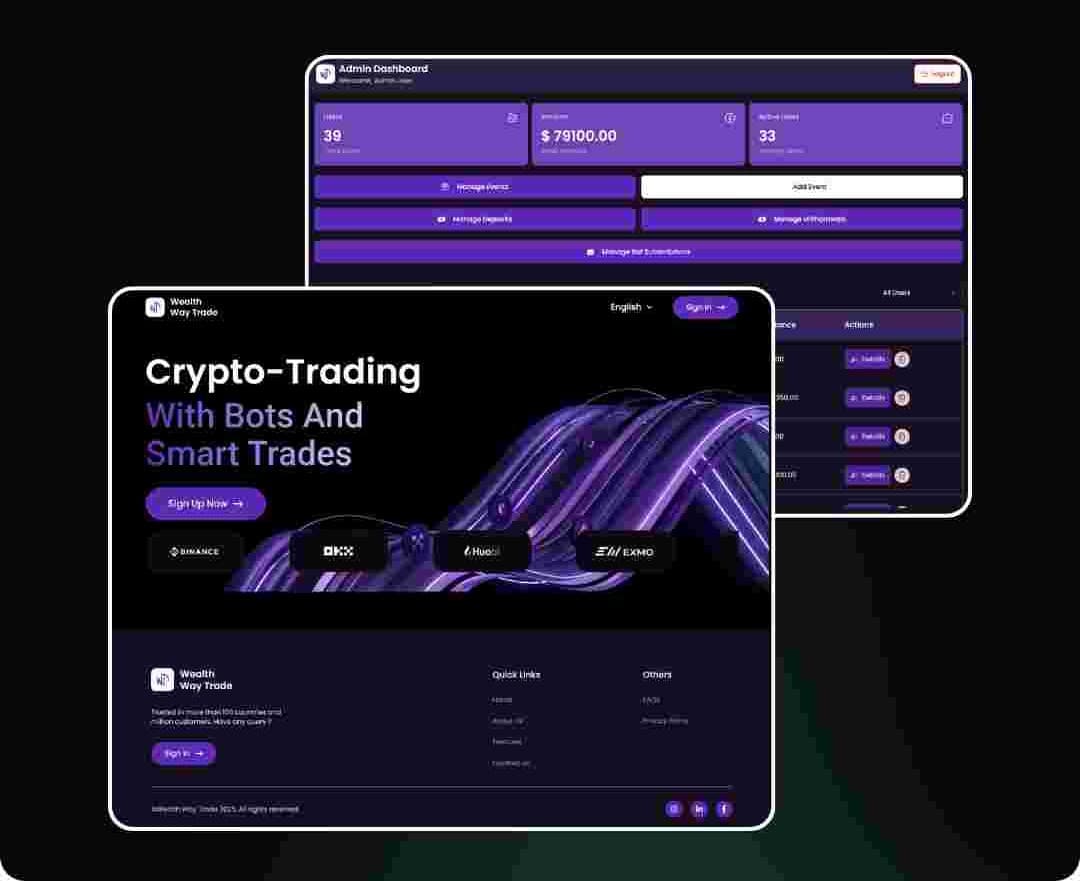
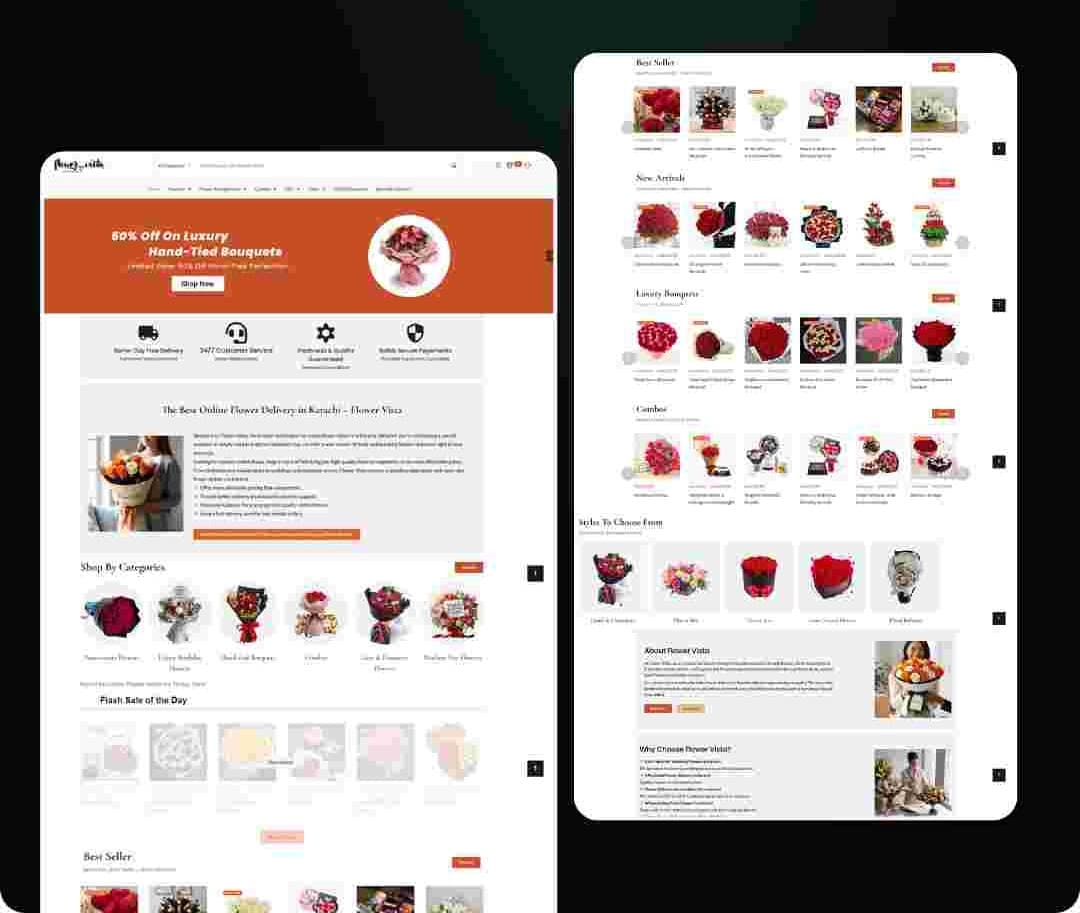
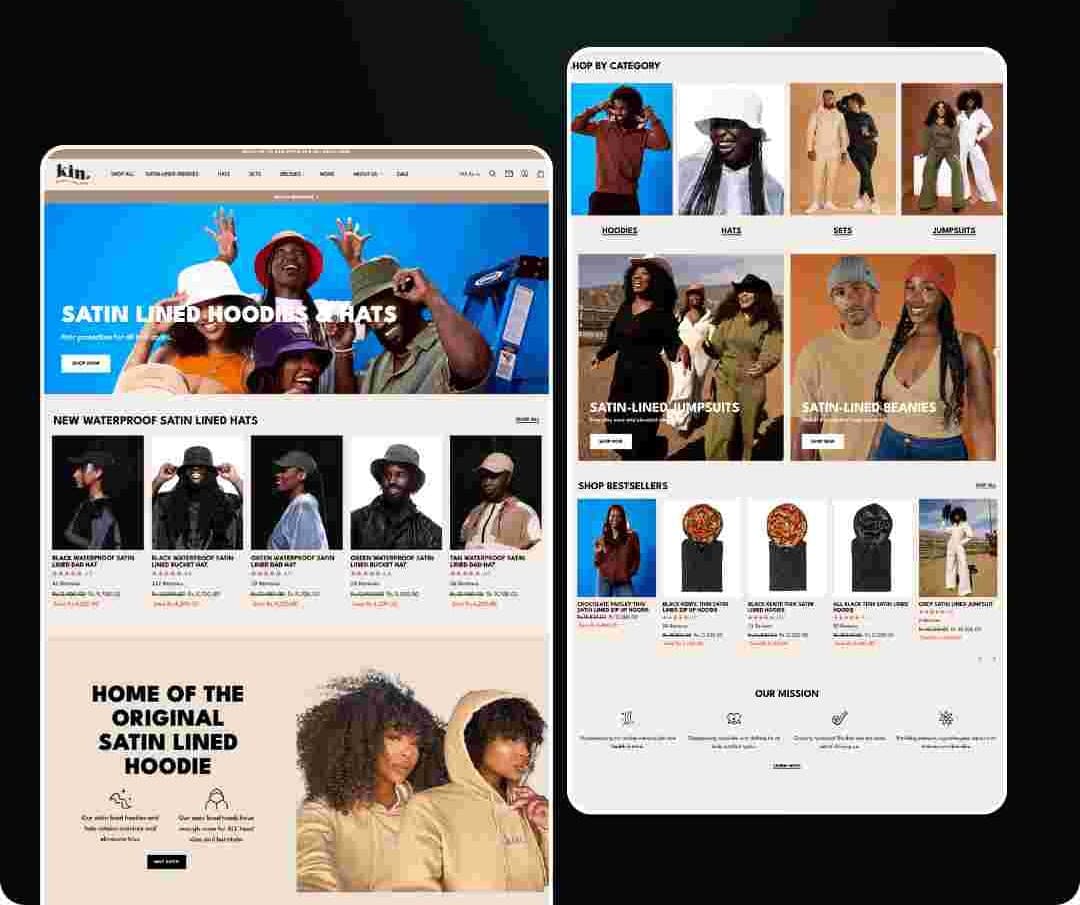
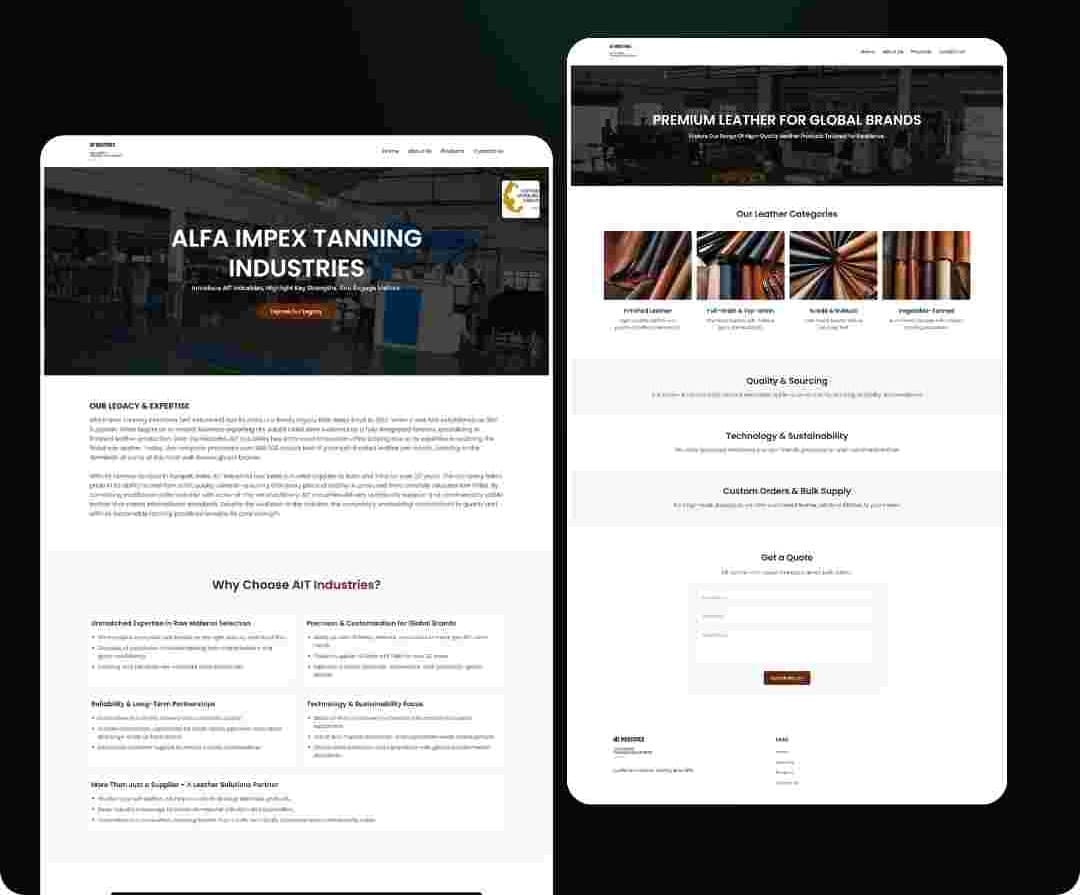
Recent Projects
We have successfully delivered a wide range of projects across various industries. Our portfolio showcases our expertise in web and mobile app development, digital marketing, and custom software solutions.